12 Most Used Operating systems by hackers
Hey Guys! Welcome
➤Here Are The Top 12 Operating Systems Used By Both Ethical And Black Hat Hackers
Penetration testing is becoming increasingly important for organizations of all sizes, as security breaches continue to grow both in frequency and in the amount of damage they cause. Hackers are always on the lookout for vulnerabilities in a computer system or network that can be easily breached and exploited.
There are some hackers who hack for the pure pleasure of hacking, while there are some who identify system vulnerabilities and access points for penetration, and prevent unwanted access to network and information systems and in return get lucratively paid for doing so. Then, there are those hackers who just want to exploit, embarrass and expose.
So, which operating systems do you think hackers enjoy exploiting the most? Since most of the operating systems for hacking is based on Linux kernel, which means that Linux is always the favorite operating system for hackers.
There are some hackers who hack for the pure pleasure of hacking, while there are some who identify system vulnerabilities and access points for penetration, and prevent unwanted access to network and information systems and in return get lucratively paid for doing so. Then, there are those hackers who just want to exploit, embarrass and expose.
So, which operating systems do you think hackers enjoy exploiting the most? Since most of the operating systems for hacking is based on Linux kernel, which means that Linux is always the favorite operating system for hackers.
1.) Kali Linux
Kali Linux is an open source project that is installable. However, the general concept is to make use of it from the live session, running all sorts of probes and tests and investigations against network targets and offline local storage. It’s geared up both with Windows and Linux-oriented tools. It also supports Wireless 802.11 frame injection, one-click MANA Evil Access Point setups, HID keyboard (Teensy like attacks), as well as Bad USB MITM attacks.
Further, Kali Linux updates its tools, and it is available for different platforms like VMWare, ARM and many more. Also, Kali is pre-installed with the best programs and security tools like Hydra (login cracker), Nmap (port analyzer), Wireshark (data packet analyzer), John the Ripper (password cracking tool) and Metasploit Framework (exploit code developing tool), and other tools that make it different from the other penetration testing operating systems.
Download Kali Linux
 Developed by the Frozenbox Team, Parrot Security OS (or ParrotSec) is a GNU/LINUX distribution based on Debian with a focus on computer security is another hackers’ favorite operating system. It is designed for penetration testing (computer security), vulnerability assessment and mitigation, computer forensics and anonymous web browsing.
Developed by the Frozenbox Team, Parrot Security OS (or ParrotSec) is a GNU/LINUX distribution based on Debian with a focus on computer security is another hackers’ favorite operating system. It is designed for penetration testing (computer security), vulnerability assessment and mitigation, computer forensics and anonymous web browsing.Parrot uses Kali repositories in order to take latest updates for almost all the tools, but it also has its own dedicated repository where all the custom packets are kept. This is why this distro is not just a simple Kali “mod” but entire new concept which relies on Kali’s tool repositories. As such, it introduces a lot of new features and different developing choices. Parrot uses MATE as a Desktop Environment. Lightweight and powerful interface is derived from famous Gnome 2, and thanks to FrozenBox’s highly customizable captivating icons, ad-hoc themes and wallpapers.
The project is certified to run over machines which have 265MB of RAM at least and it is suitable to both 32-bit (i386) and 64-bit (amd64), with a special edition it works on old 32-bit machines (486). Moreover, the project is available for armel and armhf architectures. It even offers an edition (both 32-bit and 64-bit) developed for servers only to carry out cloud pentesting.
Download Parrot Security OS
3. )BackBox

BackBox is a penetration test and security assessment oriented Ubuntu-based Linux distribution providing a network and informatic systems analysis toolkit. BackBox desktop environment includes a complete set of tools required for ethical hacking and security testing.
BackBox is lightweight OS and requires less hardware specification. The main aim of BackBox is providing an alternative, highly customizable and well performing system. It runs a desktop environment based on the lightweight Xfce window manager, which makes it standard and easy to use. It includes some of the most used security and analysis Linux tools, aiming for a wide spread of goals, ranging from web application analysis to network analysis, from stress tests to sniffing, also including vulnerability assessment, computer forensic analysis and exploitation.
BackBox has its own software repositories, which is always kept updated to the latest stable version of the most used and best known ethical hacking tools. The integration and development of new tools in the distribution follows the open source community, particularly the Debian Free Software Guidelines criteria.
Download BackBox
4.) DEFT Linux
 DEFT (Digital Evidence and Forensic Toolkit) is an open source distribution of Linux built around the DART (Digital Advanced Response Toolkit) software and based on the Ubuntu operating system. It is a distribution made for Computer Forensics, with the purpose of running live on systems without tampering or corrupting devices (hard disks, pendrives, etc…) connected to the PC where the boot process takes place. It is loaded with the best free and open source applications dedicated to incident response, cyber intelligence, computer forensics, and designed for use by the military, law enforcement, private security professional and IT auditors.
DEFT (Digital Evidence and Forensic Toolkit) is an open source distribution of Linux built around the DART (Digital Advanced Response Toolkit) software and based on the Ubuntu operating system. It is a distribution made for Computer Forensics, with the purpose of running live on systems without tampering or corrupting devices (hard disks, pendrives, etc…) connected to the PC where the boot process takes place. It is loaded with the best free and open source applications dedicated to incident response, cyber intelligence, computer forensics, and designed for use by the military, law enforcement, private security professional and IT auditors.Download DEFT Linux
5.)Caine
Caine is an Ubuntu-based security-focused distro that is available as a live disk. It stands for Computer Aided Investigation Environment and can also be run from the hard disk after installation. This Linux distro comes with a wide range of tools to help you in system forensics.
 Caine comes with a large number of database, memory, forensics, and network analysis applications. This distro for ethical hacking also features common applications like web browsers, email clients, document editors etc. for usual computing purposes.
Caine comes with a large number of database, memory, forensics, and network analysis applications. This distro for ethical hacking also features common applications like web browsers, email clients, document editors etc. for usual computing purposes.
Download Caine
6.) Samurai Web Testing Framework

The Samurai Web Testing Framework is a virtual machine that is supported on VirtualBox and VMWare, and has been pre-configured to function as a web pen-testing environment. The VM contains the best of the open source and free tools that focus on testing and attacking websites. It also includes many other tools, such as WebScarab, ratproxy, w3af, Burp Suite, and BeEF. It’s often called the best operating system for Web Penetration Testing.
Download Samurai Web Testing Framework
7.) Live Hacking OS

Live Hacking DVD is a Linux distribution filled with tools and utilities for ethical hacking, penetration testing and countermeasure verification. Based on Ubuntu, this ‘Live DVD” runs directly from the DVD and doesn’t require installation on your hard-drive. Once booted, you can use the included tools to test, check, ethically hack and perform penetration tests on your own network to ensure that it is secure from outside intruders.
The distribution comes in two forms. A full Linux desktop including a graphical user interface (GNOME) and applications like Firefox along with tools and utilities for DNS enumeration, reconnaissance, foot-printing, password cracking and network sniffing. For greater accessibility, there is a Live Hacking menu to help you quickly find and launch the tools.
The second variation is the Live Hacking Mini CD, which is command line only. However, this doesn’t detract from the power of the tools and utilities included as most of the penetration testing and ethical hacking tools are command line tools. The included /lh directory has symbolic links to the different tools included. It also requires very less hardware requirements.
For example, a fast Pentium 3 or any Pentium 4 class processor (or greater) is sufficient. For the desktop version, 512MB of memory is required with 1GB recommended. Further, the command line version just needs 128MB of memory.
Download Live Hacking OS
8.) Network Security Toolkit

Network Security Toolkit NST is a bootable ISO image (Live DVD/USB Flash Drive) based on Fedora 24 providing easy access to best-of-breed Open Source Network Security Applications and which should run on most x86_64 systems. NST provides security toolkit for professionals and network administrator with a comprehensive set of Open Source Network Security Tools. All the majority tools mentioned in the article “Top 125 Network Security Tools” by Insecure.org are included inside NST. It also comes with an advanced Web User Interface (WUI) provided for system/network administration, navigation, automation, network monitoring, host geo-location, network analysis and configuration of many network and security applications found within the NST distribution. We can say that NST Control Panel is in a web form. NST can also be used as a network security analysis, validation and monitoring tool on enterprise virtual servers hosting virtual machines.
Download Network Security Toolkit
9.) NodeZero
 NodeZero is an open source Linux kernel-based operating system derived from the world’s most popular distribution of Linux, Ubuntu, which can be used for penetration testing. NodeZero uses Ubuntu repositories, so your system will always be up to date. The system setup is basic and it is primarily designed for disk installation and customization as you want.
NodeZero is an open source Linux kernel-based operating system derived from the world’s most popular distribution of Linux, Ubuntu, which can be used for penetration testing. NodeZero uses Ubuntu repositories, so your system will always be up to date. The system setup is basic and it is primarily designed for disk installation and customization as you want.With NodeZero comes around 300 tools for penetration testing and set of basic services which are needed in penetration testing. The distro is available for download as a dual-arch Live DVD ISO image, which will run well on computers that support both 32-bit (x86) and 64-bit (x86_64) instruction set architectures.
Download NodeZero
10.) Pentoo

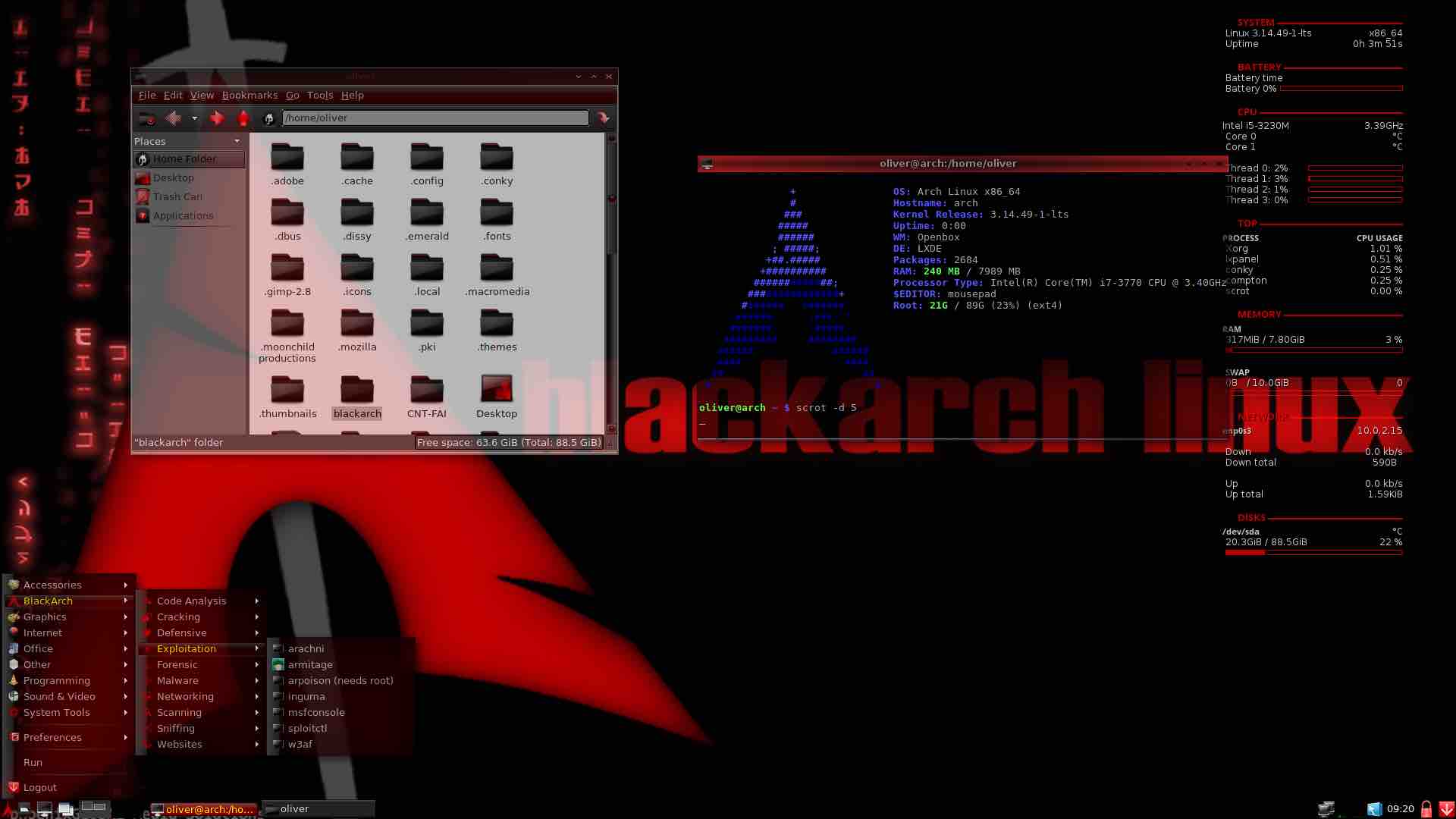 The constantly growing repo of this useful operating system for hacking purposes is stuffed with more than 1400 tools that are thoroughly tested before being added to the codebase.
The constantly growing repo of this useful operating system for hacking purposes is stuffed with more than 1400 tools that are thoroughly tested before being added to the codebase.
Download BlackArch Linux
12.) Bugtraq

Bugtraq is an electronic mailing list dedicated to issues about computer security. On-topic issues are new discussions about vulnerabilities, vendor security-related announcements, methods of exploitation, and how to fix them. It is a high-volume mailing list, and almost all new vulnerabilities are discussed there. This forum provides a vehicle for software and system manufacturers to communicate in a targeted fashion with their installed base to inform them of new vulnerabilities, so they can be addressed as soon as possible. With a team of experienced hackers and developers, they offer a great service for ethical hackers and pen testers. It is available in Debian, Ubuntu and OpenSuSe in 32 and 64 bit architectures. Bugtraq system offers the most comprehensive distribution, optimal, and stable with automated services manager in real time.
Download Bugtraq



No comments:
Post a Comment